Azure AD Authentication
RPGM Server can authenticate users from an Azure AD application.
Warning
For the Azure AD authentication, your server must be accessible in HTTPS from Internet. See the HTTPS guide to configure HTTPS in RPGM Server.
How it works
The Azure authentication uses the OAuth 2.0 protocol with Azure to authenticate users. Here is a summary of how it works:
- User clicks on "Login with Azure" ;
- He is redirected on a login page on Microsoft's Azure AD servers ;
- The user enters its credentials, his browser then receives a unique token and he is redirected on RPGM Server ;
- The user's browser send this unique token to RPGM Server which can then verify the user's identity with another API call to Azure AD servers ;
- The user is now correctly logged in.
Creating an Azure App
To configure Azure AD authentication, you first need to connect to Azure portal, then go in the Azure Active Directory section, then App registrations in the left menu.
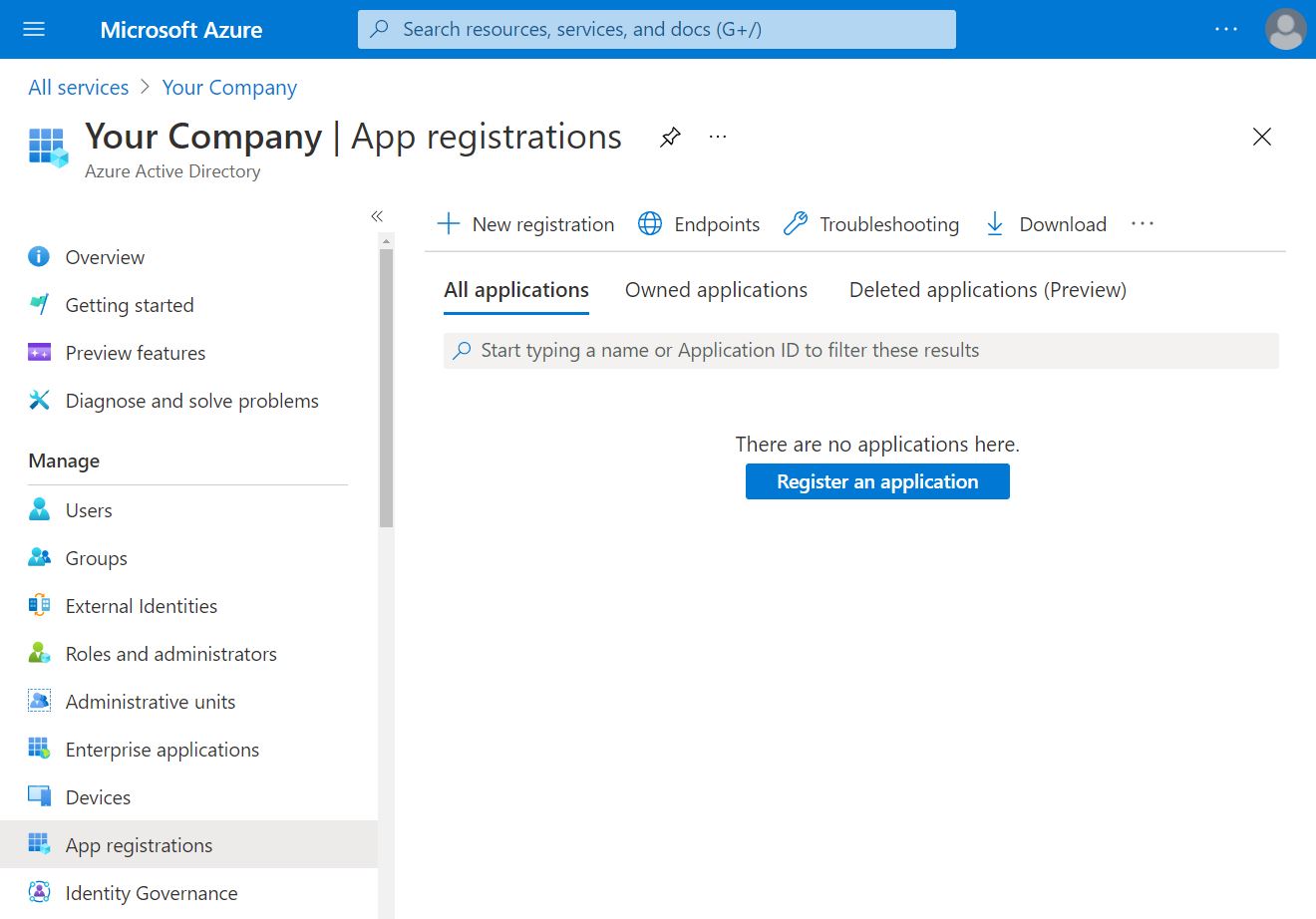
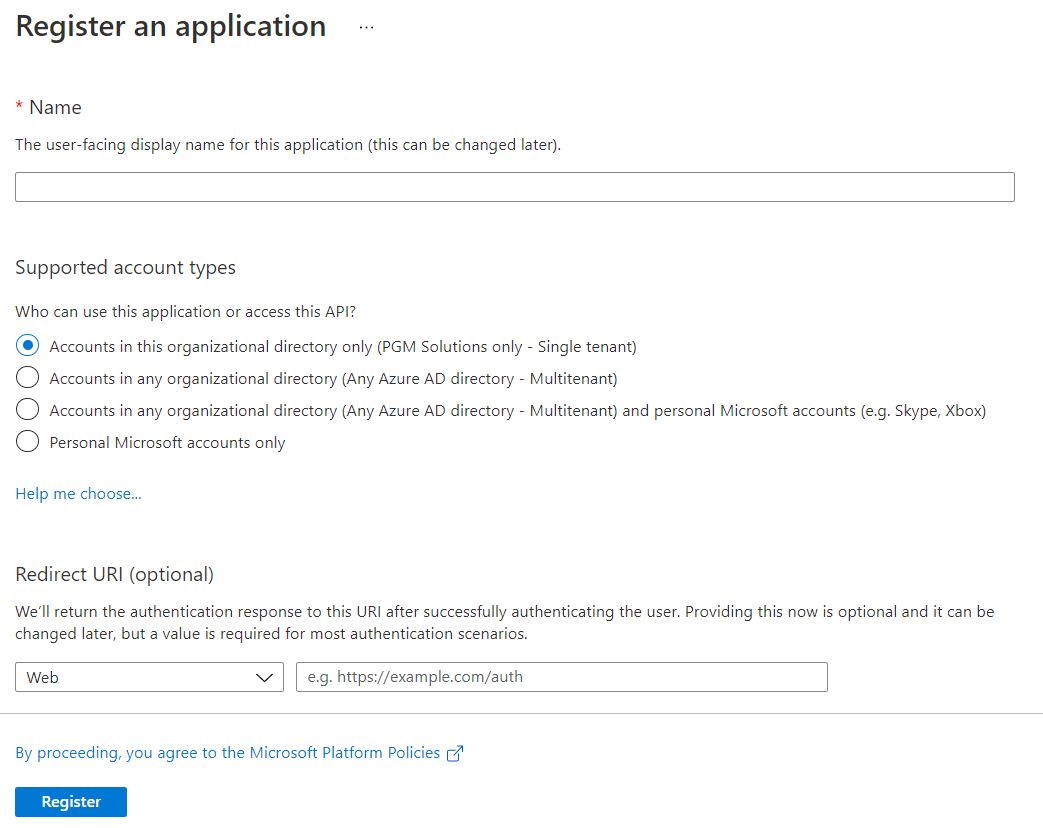
Click on the Register new application button, a new menu will pop where you have to fill a name. It is recommended to let the default Single tenant option selected for the account types.
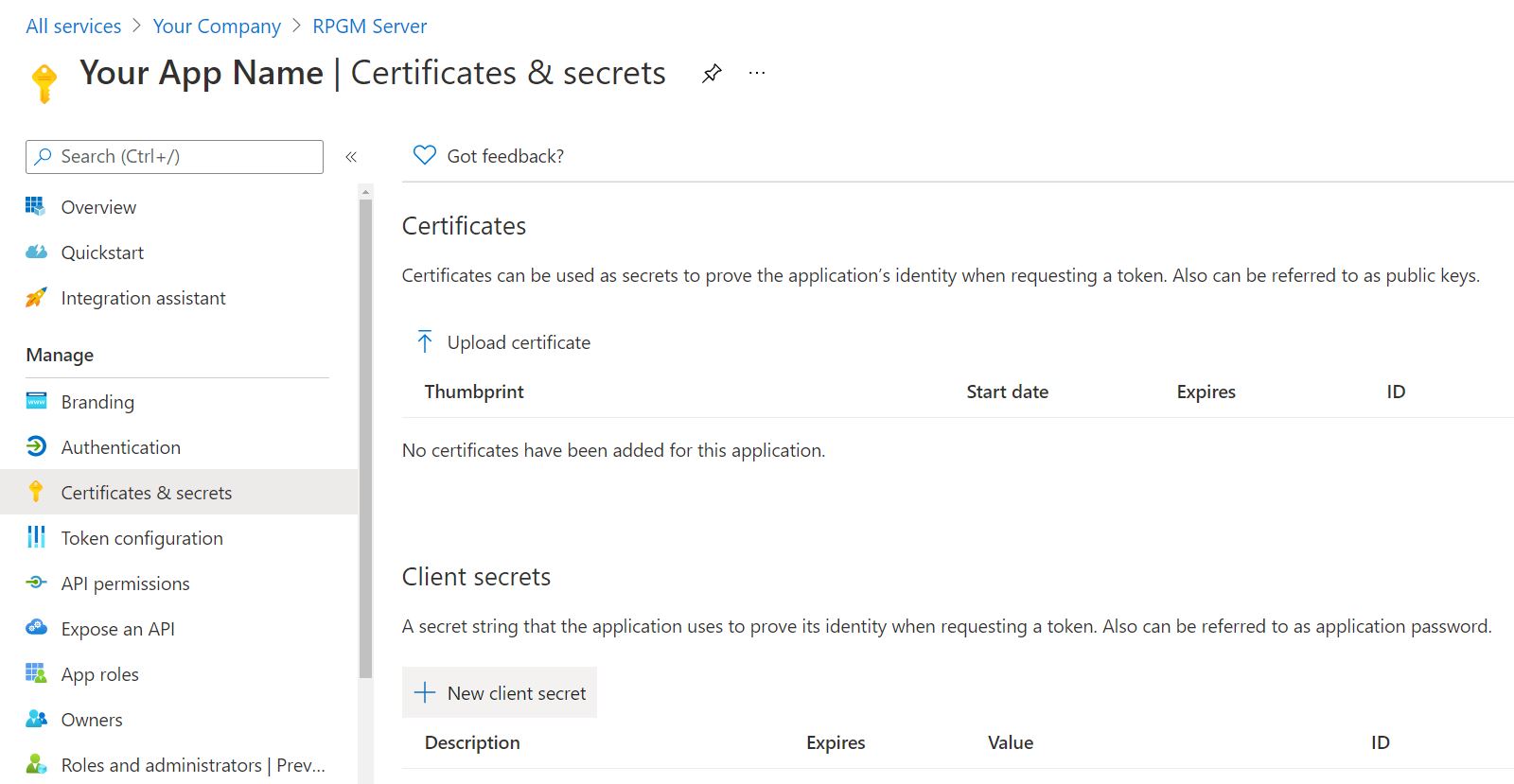
Getting Client ID and Secret
You will then be redirected on the settings page of your new app. You will find the ID of your app in the Overview section in the left menu, below the Application (client) ID entry. This is the value that should go in the authAzureADClientID in the configuration file.
In the Certificates & secrets page from the left menu, press the New client secret button to generate a new private key that should go in the authAzureClientSecret setting of the configuration file.
Configure App
In the left menu, click on Authentication, then Add a platform in the new page. In the new right window, select Web.
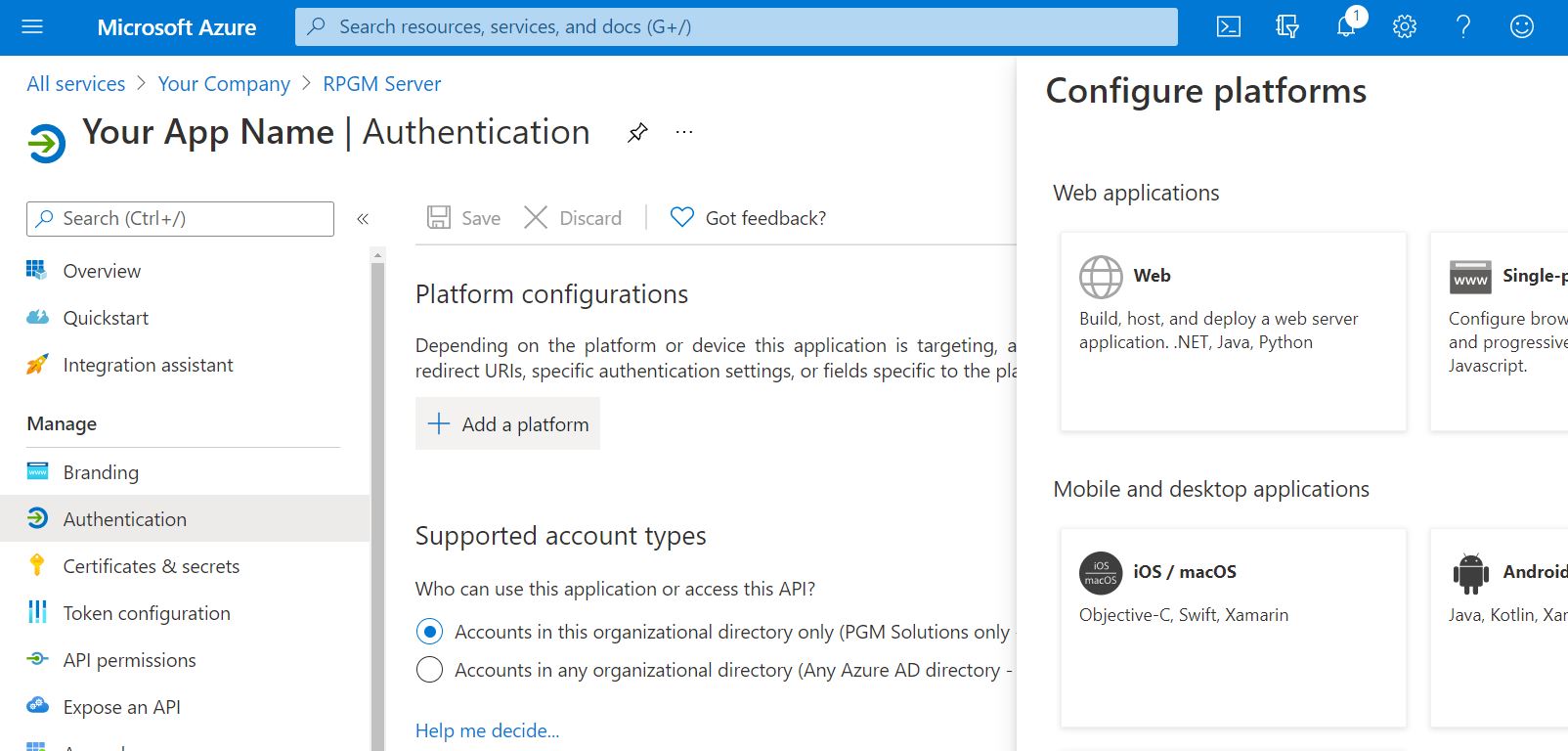
Finally, enter the complete RPGM Server address, followed by /auth/azureoauth2/callback in the Redirect URIs. For example, if your RPGM Server is installed on http://rpgm.example.com, you will want to enter https://rpgm.example.com/auth/azureoauth2/callback. Click on Configure to save your settings.
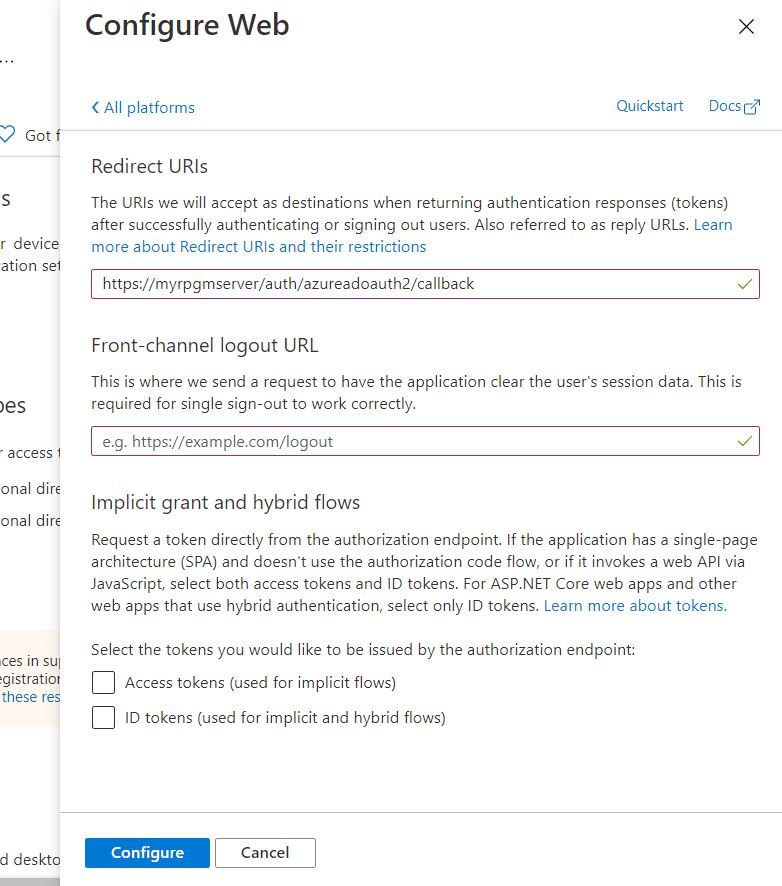
Configuring RPGM Server
Do not forget to change your configuration file within the RPGM Server folder. The settings for the Azure authentication are:
| Setting | Description |
|---|---|
| authAzureAD | Set to true if you want Azure AD Authentification. |
| authAzureADClientID | The client ID of your Azure AD App. |
| authAzureADClientSecret | The secret key of your Azure AD App. |
| authAzureADResource | Resource of your Azure AD App. Can be empty. |
| authAzureADTenant | The tenant name of your Azure AD App. Generally in the company.onmicrosoft.com format. |
| authAzureADCommonEndpoint | true if you want to use the generic, multi-domain Azure login page. Generally set to false. |
Here is an example of configuration:
# Azure AD
authAzureAD: true
authAzureADClientID: 'ID_OF_YOUR_APP'
authAzureADClientSecret: 'SECRET_OF_YOUR_APP'
authAzureADResource: ''
authAzureADTenant: 'company.onmicrosoft.com'
authAzureADCommonEndpoint: false
Do not forget to restart RPGM Server to apply the new settings.